5.0 Risk Management
My study notes for the CompTIA Security+ cert.
5.0 Risk Management
- Standard operating procedure: A document that provides step-by-step instructions on how to perform common tasks or routine operations.
- Agreement types:
- BPA (Business partners agreement): A written agreement detailing the relationship between business partners including their obligations.
- SLA (Service level agreement): An agreement between a company and a vendor that stipulates performance expectations.
- ISA (Interconnection security agreement): Specifies technical and security requirements for planning, establishing, maintaining and disconnecting a secure connection between two or more entities.
- MOU/MOA (Memorandum of understanding/agreement): Expresses and understanding between two or more parties indicating their intention to work together toward a common goal.
- Personnel management:
- Mandatory vacations: A policy that forces employees to take a vacation to deter malicious activity.
- Job rotation: A process that ensures employees rotate through different jobs to learn the processes and procedures in each job.
- Separation of duties: A security principle that prevents any single person or entity from controlling all the functions of a critical or sensitive process.
- Clean desk: A security policy requiring employees to keep their areas organized and free of papers.
- Background checks: A check into a person’s history to determine eligibility for a job.
- Exit interviews: An interview conducted with departing employees just before they leave an organization.
- NDA (Non-disclosure agreement): An agreement that is designed to prohibit personnel from sharing proprietary data.
- Onboarding: The process of granting individuals access to an organization’s computing resources after being hired.
- Continuing education: Personnel need to regularly receive additional training to ensure they are up to date on current threats, vulns and technologies.
- Acceptable use policy/rules of behavior (AUP): A policy defining proper system usage and the rules of behavior for employees.
- Adverse actions: Actions that denies employment based on the background check.
- Role-based awareness training: Targeted to personnel based on their role before getting access to minimize the risk of threats.
- Data owner: Executive level manager, responsible for data security.
- System administrator: Are responsible for the overall security of a system and enable the applications and data.
- System owner: Executive level manager, has overall responsibility for the system.
- User roles:
- User: The application user, has least privileged access to the application and data.
- Privileged user: Additional application and data permissions.
- Executive user: Responsible for the overall operation of the application, makes decisions and evaluates goals.
- Incident response team: Responsible for handling incidents within the department.
- General security policies:
- Social media networks/applications: People sharing their personal data that can result in inadvertent information disclosure or give attackers information to launch social attacks.
- Personal email: Some organizations allow employees to use the organization’s infrastructure to use their personal email, while others forbid it.
5.2 Summarize business impact analysis concepts.
- BIA (Business impact analysis): It helps an organization identify critical systems and components that are essential to the organization’s success.
- RTO (Recovery time objective): Identifies the maximum amount of time it should take to restore a system after an outage.
- RPO (Recovery point objective): Refers to the amount of data you can afford to lose.
- MTBF (Mean time between failures): Identifies the average time between failures with the goal of predicting potential outages.
- MTTR (Mean time to recover): Identifies the average time it takes to restore/repair a failed system.
- Mission-essential functions (MEF): A set of functions that must be continued throughout, or resumed rapidly after a disruption of normal operations.
- Single point of failure: A component within a system that can cause the entire system to fail if the component fails.
- Impact: The magnitude of harm related to a risk.
- Life: The most important consideration.
- Property: The risk to buildings and assets.
- Safety: Some environments are too dangerous to work.
- Finance: The resulting financial cost.
- Reputation: An event can cause status or character problems.
- Privacy impact assessment (PIA): Attempts to identify potential risks related to the PII by reviewing how the information is handled.
- Privacy threshold assessment (PTA): Helps the organization identify PII within a system.
5.3 Explain risk management processes and concepts.
- Threat assessment: An evaluation of potential threats.
- Environmental: Tornado, hurricane, earthquake…
- Man-made: Threats from humans.
- Internal vs external: Internal threats from employees or external threats from outside the organization.
- Risk assessment
- SLE (Single loss expectancy): The cost of any single loss.
- ALE (Annual loss expectancy): Is the value of SLE x ARO.
- ARO (Annual rate of occurrence): Indicates how many times the loss will occur in a year.
- Asset value: Identifies the value of an asset and can include any product, system, resource, or process.
- Risk register: A document listing information about risks.
- Likelihood of occurrence: The probability that something will occur.
- Supply chain assessment: An evaluation of the supply chain needed to produce and sell a product.
- Quantitative: A risk assessment that uses specific monetary amounts to identify cost and asset value.
- Qualitative: A risk assessment that uses judgment to categorize risks.
- Testing: It’s important to obtain vulnerability testing authorization and penetration testing authorization before performing any testing.
- Risk response techniques: Methods used to manage risks.
- Accept: When the cost of a control outweighs a risk, an organization will often accept the risk.
- Transfer: The organization transfers the risk to another entity.
- Avoid: An organization can avoid a risk by not providing a service or not participating in a risky activity.
- Mitigate: The organization implements controls to reduce risks.
- Change management: The process used to prevent unauthorized changes.
5.4 Given a scenario, follow incident response procedures.
- Incident response plan (IRP): Provides more detail than the incident response policy.
- Documented incident types/category definitions: Helps employees identify the difference between an event and an actual incident.
- Roles and responsibilities: Many incident response plans identify specific roles for an incident response team along with their responsibilities.
- Reporting requirements/escalation: Depending on the severity of the incident, sec personnel might need to escalate it or notify executives within the company of the incident.
- Cyber-incident response teams: A cyber-incident response team is composed of employees with expertise in different areas.
- Exercises: One method of preparing for incident response is to perform exercises.
- Incident response process
- Preparation: This phase occurs before an incident and provides guidance to personnel on how to respond to an incident.
- Identification: All events aren’t security incidents so when a potential incident is reported, personnel take the time to verify it is an actual incident.
- Containment: After identifying an incident, sec personnel attempt to isolate or contain it.
- Eradication: After containing the incident, it’s often necessary to remove components from the attack.
- Recovery: During the recovery process, admins return all affected systems to normal operation and verify they are operating normally.
- Lessons learned: After personnel handle an incident, sec personnel perform a lessons learned review.
5.5 Summarize basic concepts of forensics.
- Order of volatility: The order in which you should collect evidence.
- Order: Cache memory, regular RAM, swap or paging file, hard drive data, logs stored on remote systems and archived media.
- Chain of custody: A process that provides assurances that evidence has been controlled and handled properly after collection.
- Legal hold: Refers to a court order to maintain different types of data as evidence.
- Data acquisition and preservation:
- Capture system image: A forensic image of a disk captures the entire contents of the drive.
- Network traffic and logs: Helps re-create events leading up to and during the incident.
- Capture video: Video surveillance methods are used as a detective control during an investigation.
- Record time offset: An offset used by recorders to identify times on recordings.
- Take hashes: To provide proof that collected data has retained integrity.
- Screenshots: For capturing exactly what a user was doing or specific displays.
- Witness interviews: Provide firsthand reports of what happened and when it happened.
- Recovery: Extracting data that has been intentionally or accidentally deleted.
- Strategic intelligence/counterintelligence gathering: A plan for increasing the amount of data that they collect.
- Active logging: This strategy increases the amount of logged data collected on a routine basis.
- Track man-hours: Identify how much time and money is needed for a budget request.
5.6 Explain disaster recovery and continuity of operation concepts.
- Recovery sites: An alternate processing site that an organization can user after a disaster.
- Hot site: Includes everything needed to be operational within 60 minutes.
- Warm site: A compromise between an expensive hot site and a cold site.
- Cold site: Will have power and connectivity needed for activation, but little else.
- Order of restoration: After the disaster has passed, the least critical functions go to the primary site first.
- Backups: Copies of data created to ensure that if the original data is lost or corrupted, it can be restored.
- Types:
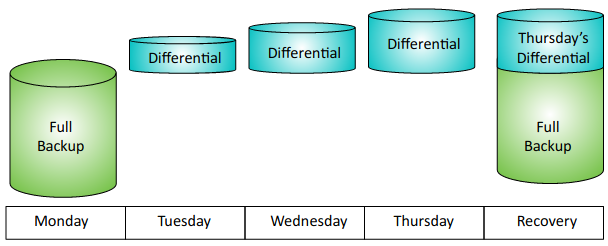
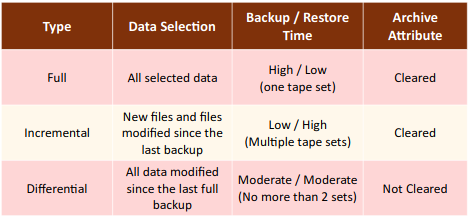
- Differential: Backs up all the data that has changed or is different since the last full backup.
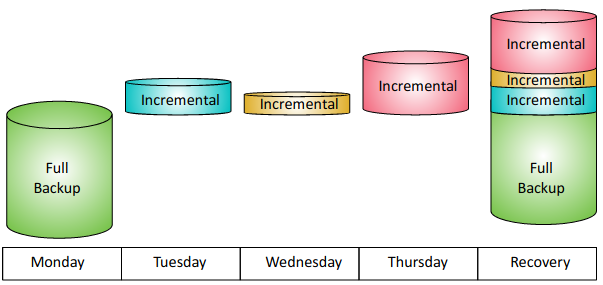
- Incremental: Backs up all the data that has changed since the last full or incremental backup.
- Snapshots: Captures the data at a point in time.
- Full: Backs up all the selected data.
- Geographic considerations:
- Off-site backups: A copy of a backup should be stored in a separate location.
- Distance: Depends on the organization, the off-site location will be close or far away.
- Location selection: Depends on the environmental issues like earthquake zones.
- Legal implications: Depends on the data stored, the backup will be protected according to gob laws.
- Data sovereignty: The legal implications when data is stored off-site.
- Continuity of operation planning: It focuses on restoring mission-essential functions at a recovery site after a critical outage.
- Exercises/tabletop: A discussion-based exercise where participants talk through an event while sitting at a table.
- After-action reports: The final phase of disaster recovery, includes a review of the disaster.
- Failover: The process of moving mission-essential functions to the alternate site.
- Alternate processing sites: An alternate site that the organization can use after a disaster.
- Alternate business practices: The organization can change the business practices after a disaster.
5.7 Compare and contrast various types of controls.
- Deterrent: Attempt to prevent incidents by discouraging threats.
- Preventive: Attempt to prevent security incidents.
- Detective: Attempt to detect when a vulnerability has been exploited.
- Corrective: Attempt to reverse the impact of an incident or problem after it has occurred.
- Compensating: Alternative controls used when it isn’t feasible or possible to use the primary control.
- Technical: Uses technology to reduce vulnerabilities.
- Administrative: Primarily administrative and include items such as risk and vulnerability assessments.
- Physical: Uses controls that you can physically touch.
5.8 Given a scenario, carry out data security and privacy practices.
- Data destruction and media sanitization: The organization has to ensure that the devices don’t include any data.
- Burning: Burn printed materials in an incinerator.
- Shredding: Shred papers by passing them through a shredder.
- Pulping: An additional step taken after shredding paper.
- Pulverizing: The process of physically destroying media to sanitize it.
- Degaussing: A very powerful electronic magnet that renders the data on tape and magnetic disks unreadable.
- Purging: A general sanitization term indicating that all sensitive data has been removed from a device.
- Wiping: The process of completely removing all remnants of data on a disk.
- Data sensitivity labeling and handling: Ensures that users know what data they are handling and processing.
- Confidential: Very sensitive, must be approved to view.
- Private: Internal use only, may require an NDA.
- Public: No restrictions on viewing the data.
- Proprietary: Is property of an organization.
- PII: Personally Identifiable Information is a personal information that can be used to personally identify an individual.
- PHI: Personal health information is PII that includes health information.
- Data roles: An organization often assigns specific roles to some people with specific responsibilities:
- Owner: The individual with overall responsibility for the data. CEO or department head.
- Steward/custodian: Handles the routine tasks to protect data.
- Privacy officer: An executive position within an organization.
- Data retention: Identifies how long data is retained and sometimes specifies where it is stored.
- Legal and compliance: Organizations have a responsibility to follow all laws that apply to them, and ensure that they remain in compliance.


