4.0 Identity and Access Management
My study notes for the CompTIA Security+ cert.
4.0 Identity and Access Management
4.1 Compare and contrast identity and access management concepts
- Identification, authentication, authorization and accounting (AAA):
- Identification: Finding the unique individual on the system.
- Authentication: The ability to tell if an individual is actually who they claim they are.
- Authorization: Determining what an individual can and cannot access on a system.
- Accounting: The tracking of an individual’s actions on the system.
- Multifactor authentication: Uses at least two of the factors of authentication.
- Something you are (biometric auth, difficult to change)
- Something you have (smart card, usb token, phone…)
- Something you know (password, pin, pattern…)
- Somewhere you are (location, IP, geolocation area…)
- Something you do (handwriting, typing technique, biometrics)
- Federation: The authenticating and authorizing between two parties. Ex. Logging onto Facebook with Google account.
- Single sign-on: Only uses one of the factors of authentication.
- Transitive trust: There are more than two entities, one entity is trusted because they are trusted by someone the company trusts.
- LDAP (Lightweight Directory Access Protocol): Queries information about the directory. Is a hierarchical structure; CN = Common Name, OU = Organizational Unit, DC = Domain Controller. Utilizes TCP/IP, TCP/UDP ports 389.
- Secure LDAP: LDAP over SSL/TLS, uses TCP on port 636. Does not send queries in plain text.
- Kerberos: Developed by MIT, for mutual authorization between client and server. It uses a ticket granting system for authorization. Is a government standard.
- TACACS+ (Terminal Access Controller Access Control System): Runs TCP over port 49, encrypts all parts of communication. Does not suffer due to security issues caused by RADIUS. Authorization and Authentication are separated for granular control.
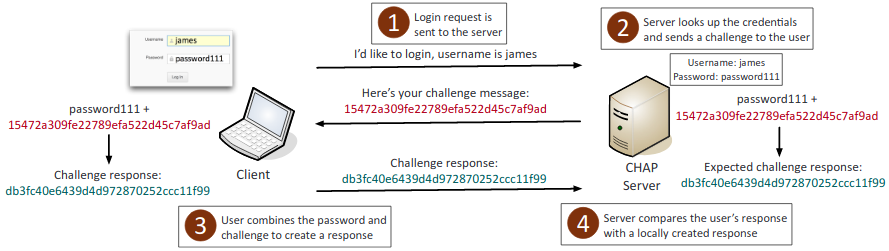
- CHAP (Challenge Handshake Authentication Protocol): Authenticates PPP clients to the server. Uses a one-way hash based on a shared secret that is compared on the client and server end. Does not send plaintext over the wire.
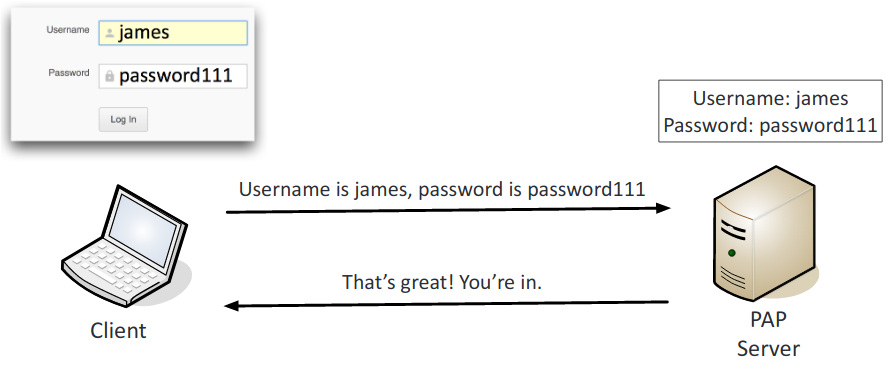
- PAP (Password Authentication Protocol): Username and password are sent as plaintext and are no longer used.
- MS-CHAP (Microsoft CHAP): Delivers a two-way, mutual authentication between the server and client. Separate keys are created for sent and received data. Is seen as weak due to it using a 5-bit encryption system, same as NTLM.
- RADIUS (Remote Authentication and Dial-in User service): Combines authentication and authorization, only encrypts the passwords, each network device must contain an authorization configuration. There is no command logging, and minimal vendor support. Uses ports 1812 for authentication and authorization and port 1813 for accounting functions.
- SAML (Security Association Markup Language): Authenticates through a third-party source to gain access, the resource is not responsible for the authentication. The request is passed through a trusted third-party server.
- The three roles are: Principle (the user or client), identity provider (the one who assures the identity of the principle), and service provider (a web service of some type.)
- OpenID Connect: OpenID Connect handles the authentication part of the identification process and uses OAuth for authorization.
- OAUTH (Open Standard for Authorization): Token authorization happens in the background. Uses a logon from a larger trusted service.
- Shibboleth: An open-source software that uses SAML to provide a third-party federated SSO authentication.
- Secure token: An authentication mechanism that can be used to identify and authenticate, and to deny and allow access.
- NTLM (New Technology LAN Manager): Used for authenticating in a Windows domain, was replaced by Kerberos for the most part.
- NTMLv2: Is the most common form used, is somewhat insecure.
4.3 Given a scenario, implement identity and access management controls.
- Access control models:
- MAC (Mandatory Access Control): Based on classification rules. Objects are given sensitivity labels, subjects given clearance labels, and users obtain access by having the correct clearance. The classifications are hierarchical.
- DAC (Discretionary Access Control): Is based on user identity. Users are granted access through ACLs placed on objects through the object’s owner or creator.
- ACL (Access Control List): A security logical device attached to all objects and resources, it defines which users are granted or denied access.
- ABAC (Attribute Based Access Control): Assigning access and privileges through a scheme of attributes. Relations and criteria determine access; time of day, location, and/or IP address.
- Role-based access control: Access is based on the job and position of the user. Changing permissions of a group changes the permissions for all of the members. Not good for companies with high turn-over rates.
- Rule-based access control: Rules are created by the admin to monitor usage and if a user needs access they must meet the requirements of the rules. Rules are enforced regardless of the user.
- Physical access control:
- Proximity cards: A smart card that does not require direct contact.
- Smart cards: Cards that contain identification/authentication information in an integrated circuit chip. Often uses dual factor authentication; something you have (the card), and something you know (a pin or password).
- Biometric factors: Verifies identity through physical features.
- Fingerprint scanner: Scans the unique patterns of the fingerprint to grant access.
- Retinal scanner: Blood vessels in the back of the retina.
- Iris scanner: Scans the Iris.
- Voice recognition: The identification and translation of spoken language for authorization of a user. Is vulnerable to impersonation.
- Facial recognition: The identification of an individual from a digital image or a video frame. Is vulnerable to impersonation.
- False acceptance rate (FAR): Incorrectly identifies an unauthorized user as an authorized user. Type 2 error.
- False rejection rate (FRR): Incorrectly identifies an authorized user as an unauthorized user. Type 1 error.
- Crossover error rate (CER): The point on a graph where the FAR and FRR meet. The lowest CER point is the most accurate biometric device for a body part.
- Tokens
- Hardware: A device that displays and constantly generates a pin or password.
- Software: An app or software that generates a token.
- HOTP/TOTP: Open source standards to generate one-time use passwords.
- HOTP (HMAC-based One-Time Password): Can be used only once before it expires.
- TOTP (Time-based One-time Password): Only last for around 30 seconds before it expires.
- Certificate-based authentication:
- PIV/CAC/smart card: Cards that have embedded certificates and a photo ID for authorization. The US DOD uses CAC/PIV.
- PIV (Personal identity verification): Is for civilians working for the federal government.
- CAC (Common access card): Is for Department of Defense members.
- IEEE 802.1x: Offers port-based authentication to wireless and wired networks to prevent rogue devices from connecting to secured ports.
- File system security: The means of ensuring that files are encrypted and can only be used by properly authorized users have access to them or modify them.
- Database security: MS and Oracle allow for the DB to be encrypted.
4.4 Given a scenario, differentiate common account management practices.
- Account types:
- User account: An account that is a collection of information that identifies an individual and grants them specific areas of the network or system.
- Shared and generic: Multiple individuals sign into a single account. No workplace should have these, cannot distinguish the actions of the user.
- Accounts/credentials:
- Guest accounts: An anonymous shared logon account.
- Service accounts: Performs specific maintenance actions, such as a backup, account and server operators.
- Privileged accounts: Access is set to access rights, generally referred to as system or network administrative accounts.
- General Concepts:
- Least privilege: Rights and permission are set to bare minimum.
- Onboarding/offboarding:
- Onboarding: Helps new employees learn all of the facets of their new job.
- Offboarding: Helps leaving employees learn how to properly leave and potentially return to the company.
- Permission auditing and review: Looks at the rights and perms assigned to users and helps ensure the principle of least privilege is enabled.
- Usage auditing and review: Logging information on what users do.
- Time-of-day restrictions: Certain privileges are permitted or restricted based on the time of day.
- Recertification: The action of regaining a certification due to the certification being expired.
- Standard naming convention: Allows for the easier identification of resource location and purpose. Reduces the amount of time needed for troubleshooting and training.
- Account maintenance: Making sure that accounts have the proper privileges, and unused accounts are deleted. Generally done through scripts to save time and money.
- Group-based access control: Every user in a group has the same privileges.
- Location-based policies: Grants and denies access based on the user’s location.
- Account policy enforcement:
- Credential management: Stores, manages, and tracks user credentials.
- Group policy: Sets different privileges of the system and allows for these to be managed or set those across entire groups or even through the entire network and every computer within it.
- Password complexity: The enforcing of complex and difficult to guess passwords.
- Expiration: The amount of time that passes before a password is required to be changed.
- Recovery: The ability to find lost passwords and usernames in case an employee forgets them.
- Disablement: Disabling an account.
- Lockout: Prevents login from specific individual after a set of failed login attempts, for a set period of time.
- Password history: Remembers past passwords and prevents the reuse of passwords.
- Password reuse: The ability to ever use the same password again.
- Password length: The minimum amount of characters that can be used in a password.
- Password age: A policy that sets how long a user can have a password before they are forced to change it.

