2.0 Technologies and Tools
My study notes for the CompTIA Security+ cert.
- Firewall: A network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- ACL (Access control lists): A list of rules that can be used to control traffic based on networks, subnets, IP addresses, ports, and some protocols.
- Application-based vs. network-based:
- Application-based: It is typically software running on a system. Protects the user from applications and services by monitoring and potentially blocking the input, output, or system service calls that do not meet the configured policy of the firewall.
- Network-based: Filters traffic by port number based on rules and allows only authorized traffic to pass in and out of the network
- Stateful vs. stateless:
- Stateful: Stateful firewalls block traffic based on the state of the packet within a session. It adds and maintains information about a user’s connections in a state table, referred to as a connection table.
- Stateless: Stateless firewalls uses rules within an ACL to identify allowed and/or block traffic through packet filtering. Does not keep track of flows.
- Implicit deny: The last rule in an ACL that indicates that, “all traffic that isn’t explicitly allowed is implicitly denied”.
- VPN concentrator: A type of router device that allows for the secure creation of VPN connections and for the safe delivery of messages between VPN nodes. Allows for the handling of a large quantity of VPN tunnels.
- Remote access vs. site-to-site:
- Remote access: A user-to-LAN connection used by remote users.
- Site-to-site: Allows multiple sites to connect to remote sites over the internet.
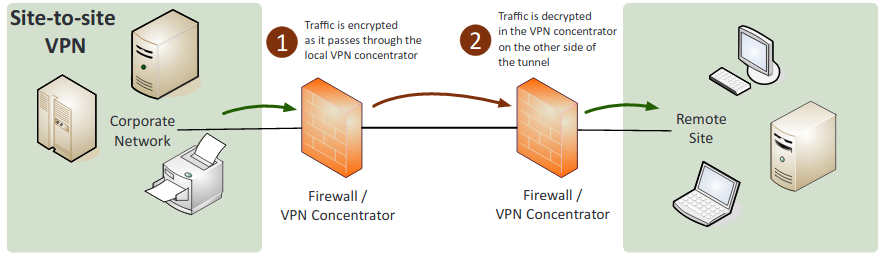
- IPSec: A protocol suite for securing Internet Protocol (IP) communications. Encrypts and authenticates all of the packets in a session between hosts or networks. Secures more applications than SSL and TLS.
- Tunnel mode: The default mode for IPSec, the entire pack is protected.
- Transport mode: Used for end-to-end communications in IPSec. Ex. encrypted Telnet or Remote Desktop session from a workstation to a server.
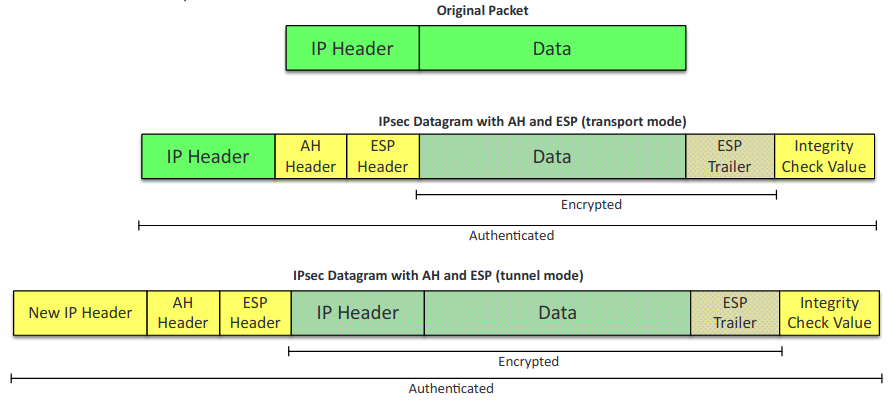
- Authentication Header (AH): IPsec protocol that authenticates that the packets received were sent from the source identified in the header. MD5, SHA-1 or SHA-2.

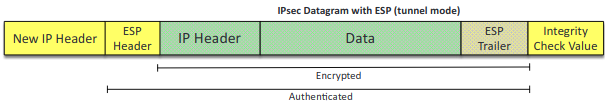
- ESP (Encapsulating Security Payload): IPSec component that provides the same services as AH and also ensures confidentiality when sending data. MD5, SHA-1 or SHA-2 for hash, 3DES or AES for encryption.
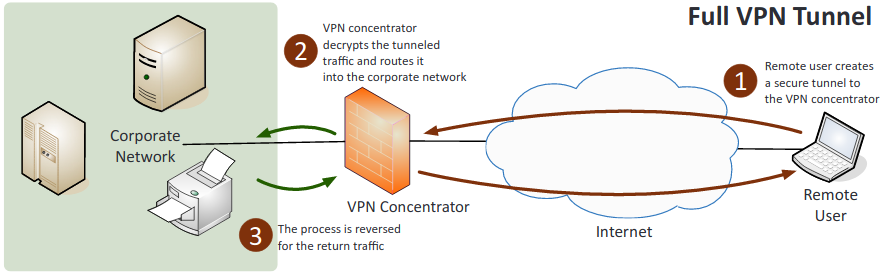
- Split tunnel vs. full tunnel:
- Split tunnel: Only some traffic over the secure VPN while the rest of the traffic directly accesses the internet.
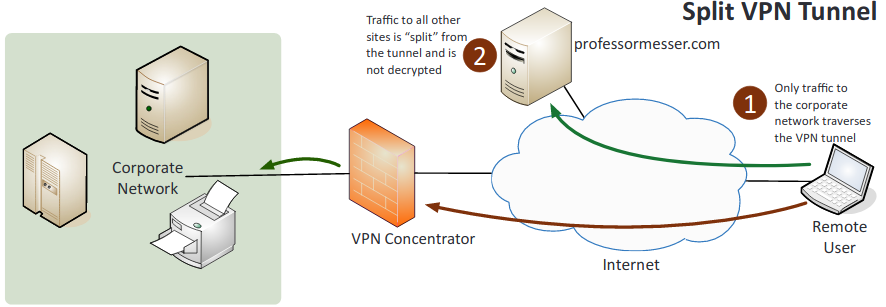
- Full tunnel: All of the traffic is sent over the secure VPN.
- TLS: The replacement of SSL to encrypt data-in-transit. Uses certificates issued by CAs.
- Always-on VPN: The user does not connect and disconnect and instead is always connected.
- NIPS (Network Intrusion Prevention System)/NIDS (Network Intrusion Detection System):
Watch network traffic.
- Signature-based: Detects attacks based on known attack patterns documented as attack signatures.
- Heuristic/behavioral: It detects attacks by comparing traffic against a baseline to find any anomalies.
- Anomaly: Abnormal packets or traffic.
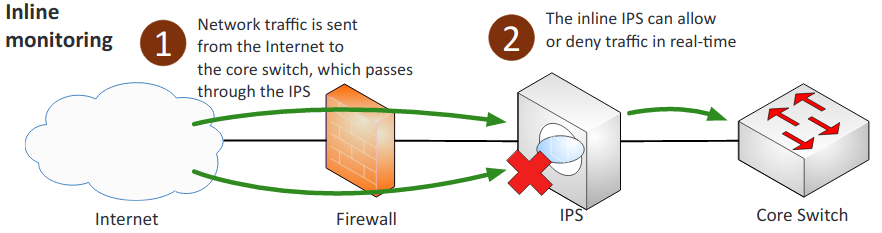
- Inline vs. passive:
- Inline: Connected directly to the network and monitors the flow of data as it occurs.
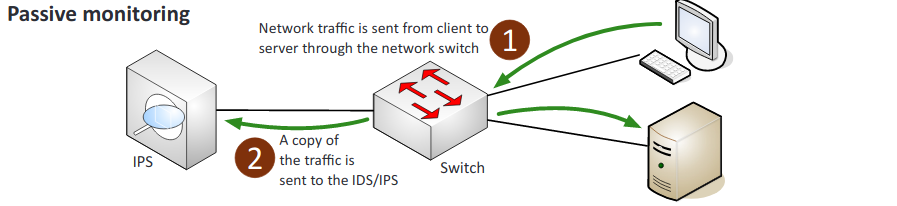
- Passive: Connected through a switch or port on the network and receives a copy of the flow of data as it occurs.
- In-band vs. out-of-band:
- In-band: Sits in the network, can quickly warn of or prevent malicious traffic.
- Out-of-band: Can only warn of malicious traffic. When identifies it, sends reset frames.
- Rules: Standards set to differentiate good traffic from suspicious traffic.
- Analytics: Shows the amount, type and history of traffic coming through.
- False positive: NIPS blocks legitimate incoming traffic.
- False negative: NIPS allows harmful incoming traffic.
- Router: A device that directs data traffic along specific routes.
- ACLs (Access Control List): A list of permit or deny rules detailing what can or can’t enter or leave the interface.
- Anti-Spoofing: Prevent a bad guy from using someone else’s address. Filter reserved IP addresses.
- Switch: A networking device that connects devices together on a computer network
- Port security: Requires a username and a password and authenticate before gaining access to any of the switch interfaces.
- Layer 2 vs. Layer 3:
- Layer 2: Packets are sent to a specific switch port based on destination MAC addresses.
- Layer 3: Packets are sent to a specific next-hop IP address, based on destination IP address.
- Loop prevention: Spanning-tree algorithms can determine the best path to a host while blocking all other paths to prevent loops. Loops can cause a denial of service.
- Flood guard: Configuration that sets the maximum number of MAC addresses that could possibly be seen on any particular interface.
- Proxy: Acts as an intermediary for requests from clients seeking resources from servers that provide those resources.
- Forward and reverse proxy:
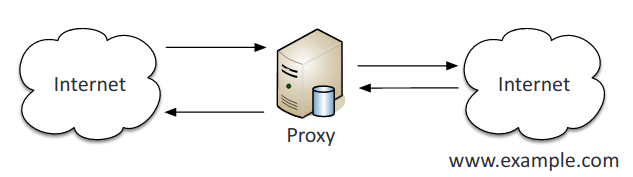
- Forward proxy: Forwards requests from internal clients to external servers.
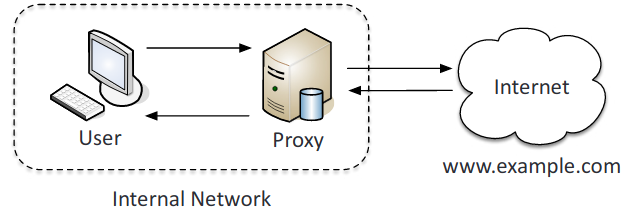
- Reverse proxy: Takes in requests from the Internet and forwards them to an internal web server.
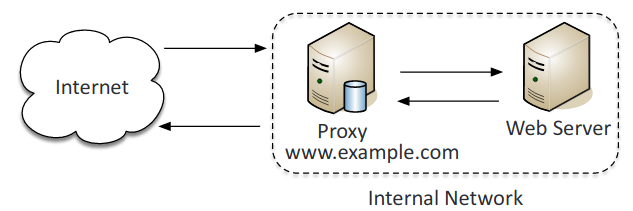
- Transparent: Accepts and forwards requests without performing any modifications on them.
- Application/multipurpose: A type of proxy server that knows the application protocols that it supports.
- Load balancer: A reverse proxy that distributes network or application traffic across a number of servers designed to increase capacity of concurrent users and reliability of applications.
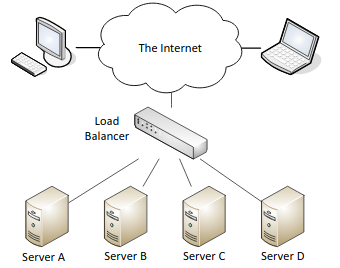
- Scheduling: Sends requests to servers using set rules.
- Affinity: Sends client requests to the same server based on the client’s IP address.
- Round-robin: Sends requests in a predefined order.
- Active-passive: Some servers are not active and only go active to take excess traffic or if an active server fails.
- Active-active: All servers are actively processing requests
- Virtual IPs: An IP address and a specific port number that can be used to reference different physical servers. Provides IP addresses that can float between two or more physical network nodes and provide redundancy.
- Access point:
- SSID: Name of a wireless network.
- MAC filtering: A method of controlling access on a wired or wireless network by denying unapproved MAC address access to a device.
- Signal strength: The quality and distance of a signal.
- Band selection/width: Can be set between 2.4 GHz and 5 GHz depending on which 802.11 protocol is being used.
- Antenna types:
- Omnidirectional: Signal is evenly distributed on all sides but has no ability to focus the signal.
- Directional: Focus the signal increasing distance. (Yagi and parabolic)
- Fat: Has everything necessary to handle wireless clients. If end-user deploys several Fat Wireless Access Points, each one needs to be configured individually.
- Thin: Acts as a radio and antenna that is controlled by a wireless switch. If multiple thin wireless access points are deployed, the entire configuration takes place at the switch. This is the far cheaper option.
- Antenna placement:
- Controller-based: Require a controller for centralized management and are not manually configured.
- Standalone: Do not require a controller and are generally used in smaller environments.
- LWAPP (Lightweight Access Point Protocol): Manages multiple access points simultaneously.
- SIEM (Security Information and Event Management):
- Aggregation: The gathering of log and event data from the different network security devices used on the network.
- Correlation: Relating various events to identifiable patterns. If those patterns threaten security, then action must be taken.
- Automated alerting and triggers: Sends messages based on configured rules based on events that occur within the log files.
- Time synchronization: Ensures that the time is the same across devices so that all security events are recorded at the same time using Network Time Protocol.
- Event de-duplication: Trimming event logging so that the same event is not recorded over and over again, overflowing log space.
- Logs/WORM: Prevents alteration of logs and archives the source logs with write protection.
- DLP (Data Loss Prevention): Policies and technologies that protect data loss through theft or destruction.
- USB blocking: Prevents the use of USBs
- Cloud-based: Prevents sensitive data from being stored on the cloud without proper encryptions and authorization.
- Email: Protects against email fraud and from valuable data from being sent through email.
- NAC (Network Access Control): Enforces security policies on devices that access networks to increase network visibility and reduce risk.
- Dissolvable vs. permanent:
- Dissolvable: Disappears after reporting information to the NAC device.
- Permanent: Resides on end devices until uninstalled.
- Host health checks: Reports sent by network access control to gather information on installeddevices.
- Agent vs. agentless:
- Agent: Is installed on the end device.
- Agentless: Is not installed on the device itself but instead is embedded within a Microsoft Windows Active Directory domain controller.
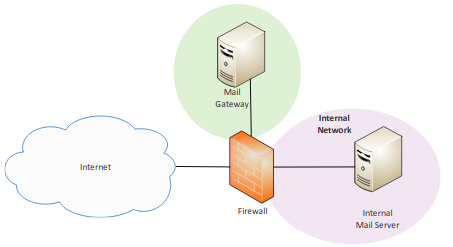
- Mail gateway: Examines and processes all incoming and outgoing email.
- Spam filter: An on-premises software solution for filtering, well spam emails.
- DLP (Data Loss Prevention): Prevents certain information leaving the organization via email.
- Encryption: Encrypt and decrypts emails being sent and received across networks.
- Bridge: Provides interconnection with other bridge networks using the same protocol.
- SSL/TLS accelerators: The process of offloading processor-intensive public-key encryption for TLS or its SSL to a hardware accelerator.
- SSL decryptors: Allows for the user to view inside of passing Secure HTTP traffic.
- Media gateway: Converts media streams between disparate telecommunications technologies.
- Hardware security module (HSM): Safeguards and manages digital keys for strong authentication and provides cryptoprocessing.
2.2 Given a scenario, use appropriate software tools to assess the security posture of an organization.
- Protocol analyzer: Hardware or software that captures packets to decode and analyze their contents. Allows for you to easily view traffic patterns, identify unknown traffic, and verify packet filtering and security controls.
- Big data analytics: Allows for the user to store large amounts of data and then easily go through it.
- Network scanners: A computer program used for scanning networks to obtain user names, host names, groups, shares, and services.
- Rogue system detection: Find devices that are not supposed to be on the network, such as rogue APs.
- Network mapping: Identifying all devices on a network along with a list of ports on those devices.
- Wireless scanners/cracker:
- Wireless scanners: Is for wireless monitoring, it scans wireless frequency bands in order to help discover rogue APs and crack passwords used by wireless APs.
- Wireless cracker: Uses wireless attacks to test if an attacker could find the passwords to gain access to parts of your network.
- WEP: Cryptographic vulnerabilities, is relatively straightforward.
- WPA1 PSK and WPA2 PSK: Uses dictionary brute force and rainbow tables attacks.
- Password cracker: A program that uses the file of hashed passwords, such as a rainbow table, and then attempts to break the hashed passwords of the network. Getting the hashes is the hardest part.
- Vulnerability scanner: Attempts to identify vulnerabilities, misconfigured systems, and the lack of security controls such as up-to-date patches. They can be passive or active, either way they have little impact on a system during the test.
- Configuration compliance scanner: A vulnerability scanner that verifies systems are configured correctly and meet the minimum-security configurations, it typically does this by comparing the system to a file that has the proper configurations. This is an ongoing task and can be integrated with the logon process.
- Exploitation frameworks: An already created set of exploits that already have all the major components designed, the user just needs to figure out how to inject them into the network. These tool sets can be used offensively by hackers or defensively by pen testers.
- Data sanitization tools: Tools that overwrite data on hard drives so that it is unrecoverable, this only needs to be done once but some may do it multiple times to feel safe.
- Steganography tools: Allows for the user to embed data into an image, video, sound files, or packets. It is security through obscurity.
- Honeypot: Decoy systems or networks to gather information on the attacker.
- Backup utilities: Important to protect data from being lost, downtime, or corrupted.
- Banner grabbing: The process of capturing the initial message (the banner) from a network service. Often the banner discloses the application’s identity, version information, and other sensitive information.
- Passive vs. active:
- Passive: You are observing.
- Active: You are interacting with the network by sending traffic and trying to access parts of the network.
- Command line tools:
- ping: The name is based on the sound made by sonar. Tests reachability, it is a primary troubleshooting tool.
- netstat (Network statistics):
- netstat -a: Show all active connections.
- netstat -b: Show binaries, for Windows.
- netstat -n: Does not resolve names.
- tracert (Windows)/traceroute (MacOS/Linux): Uses the ICMP (Internet Control Message Protocol) time to live (TTL) error message to map the path of a packet. Time in TTL is measured in hops, TTL = 1 for the first router, and 2 refers to the second router.
- nslookup/dig (Domain Information Groper):
- nslookup: Used to gather information from DNS servers, lookups names and IP addresses. Was replaced by dig.
- dig (Domain Information Groper): More advanced than nslookup and shows more detailed domain information. Is for Linux but can be downloaded for windows.
- arp (Address Resolution Protocol): Used to view MAC addresses.
- Arp -a: Views the local arp table.
- ipconfig/ip/ifconfig:
- ipconfig: Shows the Windows TCP/IP configuration.
- ip: Used to replace ifconfig on Linux. Shows and manipulates settings on the network interface card (NIC).
- ifconfig: Shows the Linux interface configuration.
- tcpdump: A command-line packet analyzer that allows to capture packets from the command line.
- nmap: It is designed to scan a network and create a map, this is useful as a vulnerability scanner because it can find open ports and unsecured access points.
- netcat: Is used to safely connect to remote systems using command line instead of a front-end application. Can also be used for banner grabbing.
2.3 Given a scenario, troubleshoot common security issues.
- Unencrypted credentials/clear text: All authentication must be encrypted. Unencrypted credentials can allow for the attacker to: elevate privileges, establish a foothold, maintain persistence, and move to other networks.
- Logs and events anomalies: Block all outside access until the issue is fixed, backup and preserve the current logs, and if possible, restrict access to more sensitive data till the issue is fixed.
- Permission issues: Determine how much access a specific user needs to be able to complete their job. Confirm permissions on initial configurations, perform periodic audits, and provide a process for changes and updates.
- Access violations: Segmentation fault, OS locks you out, or prevents access to restricted memory. A user is able to properly logon and then access systems they don’t have proper authorization for.
- Certificate issues: Certificates should be signed by someone trusted, be up to date, and be properly checked.
- Data exfiltration: Data is your most important asset to and attackers.
- Misconfigured devices:
- Firewall: Provide too much access, and to audit when using a large rule base.
- Content filter: URLs are not specific, and some protocols are not filtered.
- Access points: No encryption mechanisms and Open configurations from the wireless side.
- Weak security configurations: Make sure to regularly upgrade equipment and update firmware. Using hash algorithms that are susceptible to collisions.
- Personnel issues: The weakest link
- Policy violation: Transferring private data or visiting unsafe websites.
- Insider threat: Authenticated users have free reign. Assign correct user rights and permissions.
- Social engineering: Deceit can cause employees to give up personal or valuable data.
- Social media: Sharing private data or personal information.
- Personal email: Uses company resources and leaves the network vulnerable.
- Unauthorized software: Don’t know what it is: could conflict with company software, could be malware, or could be useful for work.
- Baseline deviation: Everything is well documented, any changes to the norm should be noted, and no remote access until it matches the baseline.
- License compliance violation (availability/integrity): Make sure licenses are up to date and valid.
- Asset management: Identify and track assets to respond faster to security risks. Keep detailed records of the most valuable assets. Usually automated.
- Authentication issues: The more factors the safer, makes sure the user is actually the correct person.
2.4 Given a scenario, analyze and interpret output from security technologies.
- HIDS/HIPS:
- HIDS (Host-based intrusion detection system): Runs on a single computer and alerts of potential threats to help warn of attacks against that host.
- HIPS (Host-based intrusion prevention system: Runs on a single computer and intercepts potential threats to help prevent attacks against that host.
- Antivirus: Software that is specifically designed to detect viruses and protect a computer and files from harm.
- File integrity check: An application that can verify that the files have not been modified using hash algorithms to authenticate the file.
- Host-based firewall: A firewall that is on a single host that only restricts incoming and outgoing network activity for that host.
- Application whitelisting: The practice of allowing only approved programs to run on a computer, computer network, or mobile device.
- Removable media control: Blocks users from using USB drives, CD/DVD drives or portable hard drives/flash drives to help prevent the installation of viruses, malware, and exfiltration of data.
- Advanced malware tools: Block malware from running by blocking file signature, heuristics/Anomalous behavior, sandboxing, virtualizing. Need to be routinely updated with the latest definitions to be secure and protect against current threats.
- Patch management tools: Tools that aid in the: monitoring, evaluating, testing, and installing of the most current software patches and updates.
- UTM (Unified Threat Management): A group of security controls combined in a single solution that can inspect data streams for malicious content and block it.
- DLP (Data Loss Prevention): Systems that identify, monitor, and protect data: from unauthorized use, transfers, modification, or destruction.
- Data execution prevention (DEP): Memory regions are marked as non-executable which prevents code from being executed. This protects against memory abuse attacks such as buffer overflows.
- Web application firewall: A firewall that monitors and filters packets carrying HTTP traffic using a set of communication rules.
2.5 Given a scenario, deploy mobile devices securely.
- Connection methods
- Cellular: Network used for mobile phones.
- Potential Risks: Cellular devices are susceptible to traffic monitoring, location tracking, and gain access to the device from anywhere in the world.
- WiFi: A local area network that uses high frequency radio signals to transmit and receive data over distances of a few hundred feet.
- Potential Risks: If the WiFi connection is not encrypted it is vulnerable to eavesdropping. Jamming frequencies or interferences can cause a denial of service.
- SATCOM: Satellite Communications that is used for communications in remote areas and during natural disasters.
- Potential Risks: SATCOM devices are at risk of leaking geopositioning data and remote code execution, and are not easily updated remotely.
- Bluetooth: Allows electronic devices like cell phones and computers to exchange data over short distances using radio waves.
- NFC (Near Field Communication): Enable two electronic devices in short proximity to each other. Typically used as a payment system, but can also be used as an identity token and to help pair Bluetooth devices.
- Potential Risks: Active devices can perform a remote capture up to a ten meter range. Jamming frequencies or interferences can cause a denial of service. Can be vulnerable to relay and replay attacks.
- ANT/ANT+: A wireless sensor protocol that uses a 2.4 GHz ISM (industrial, scientific, and medical) band to communicate. Used in heart monitors, sports and fitness sensors.
- Potential Risks: At risk of jamming band, and eavesdropping because encryption is vulnerable.
- Infrared: Electromagnetic waves of frequencies lower than the red of visible light. Used to control entertainment devices and other IR devices.
- USB (Universal Serial Bus): A cable used to connect mobile devices to other devices. Is comparatively safer than wireless because it requires a physical connection and data is not allowed to be transferred without being unlocked first.
- Potential Risks: Mobile devices can appear as storage devices allowing for the exfiltration and theft of data.
- Mobile device management concepts:
- Application management: Limiting which applications can be installed on a device.
- Content management: Limiting access to content hosted on company systems, and controlling access to company data stored on mobile devices.
- Remote wipe: Allows for the deletion of all data and possibly even configuration settings from a device remotely.
- Geofencing: Using GPS to define geographical boundaries where the app can be used.
- Geolocation: The location of a device identified by GPS.
- Screen locks: Prevents someone from being able to pick up and use a mobile device.
- Push notification services: Send messages to mobile devices from apps without user intervention.
- Passwords and pins: Keep the device safe with something you know.
- Biometrics: Keep the device safe with something you are.
- Context-aware authentication: Uses multiple elements to authenticate a user and a mobile device.
- Containerization: isolating and protecting the application, including any data used by the application.
- Storage segmentation: Separates the information on a device into partitions.
- Full device encryption: Scramble all of the data on the device. Protects against loss of confidentiality.
- Enforcement and monitoring for:
- Third-party app stores: Anything that isn’t from the Apple’s App Store or Google Play. More likely to be a risk to security.
- Rooting/jailbreaking:
- Rooting: Android, the process of modifying the device to gain root-level (full administrator) access.
- Jailbreaking: Apple, the process removing all software restrictions from the device.
- Sideloading: The process of copying an application package to a mobile device.
- Custom firmware: The removal of the pre-installed firmware and replacing it. This may remove bloatware included by the vendor or telco, add or remove features, and streamline the OS to optimize performance.
- Carrier unlocking: Means the device can be used by any carrier.
- Firmware OTA updates: The over the air downloading of: upgrades, patches, and improvements to the existing firmware.
- Camera use: Disable it except for certain locations to prevent espionage.
- SMS/MMS: Sending alerts through text messages.
- External media: Disable it to prevent the transferring of files through physical ports.
- USB OTG (Universal Serial Bus On-The-Go): A cable used to connect mobile devices to other devices. It is one of many methods that you can use to connect a mobile device to external media.
- Recording microphone: Disable it to prevent people from being able to listen in on conversations.
- GPS tagging: Adding GPS information to the video, photo giving its location
- WiFi direct/ad hoc: Means for wireless devices to connect directly to each other without a wireless access point.
- Tethering: The process of sharing an Internet connection from one mobile device to another.
- Payment methods: To pay for services wirelessly over a limited area.
- Deployment models:
- BYOD (Bring Your Own Device): Employees to connect their own personal devices to the corporate network to work.
- COPE (Corporate Owned, Personally Enabled): Are owned by the organization, but can be used personally by employees.
- CYOD (Choose Your Own Device): Employees can purchase devices on the list and bring them to work. The company then supports, monitors, and manages the device.
- Corporate-owned: Company owns and controls all aspects, no personal info at all, most secure for company.
- VDI (Virtual Desktop Infrastructure): A virtual desktop that is created so users can access their desktop from a mobile device.
2.6 Given a scenario, implement secure protocols.
- Protocols:
- DNS (Domain Name Service): Does not have any security in its original design. The hierarchical and decentralized naming system for computers, services, or other resources connected to a private network or the internet.
- DNSSEC (Domain Name Service Security Extensions): Primary purpose is to provide a reliable authorization service between devices when performing operations on the DNS. Must be digitally signed.
- SSH (Secure Shell): Replaces Telnet. TCP (Transmission Control Protocol) over Port 22. Allows for a securely encrypted terminal connection.
- S/MIME (Secure/Multipurpose Internet Mail Extensions): Digitally signed email content using public key encryption.
- SRTP (Secure Real-time Transport Protocol): Protected and encrypted voice communications.
- LDAPS (Lightweight Directory Access Protocol Secure): TCP ports 389 and 636. Protocol used for reading and writing directories over an IP network. Uses the X.500 specifications written by the International Telecommunications Union (ITU) over SSL/TLS.
- FTPS (File Transfer Protocol Secure): TCP Ports 989/990. File transfer using SSL/TLS.
- SFTP (Secure File Transfer Protocol): TCP Port 22. FTP over an SSH channel.
- SNMPv3 (Simple Network Management Protocol Version 3): Ports 161/162. Encrypted statistics gathering from a router.
- SSL (Secure Sockets Layer)/TLS (Transport Layer Security):
- SSL (Secure Sockets Layer): Encryption technology developed for web and email over the transport layer. Uses public keys to exchange symmetric keys.
- TLS (Transport Layer Security): The replacement for SSL, is sometimes called SSL still. Used to encrypt the communication of servers in an organization.
- HTTPS (Hypertext Transfer Protocol Secure): TCP port 443. HTTP over SSL/TLS provides a secure connection between the server and web browser.
- Secure POP (Post Office Protocol)/IMAP (Internet Message Access Protocol):
- Secure POP (Post Office Protocol): Sends from port 110 to 995. Encrypted email communications used for retrieving email from a mail server over SSL/TLS.
- Secure IMAP (Internet Message Access Protocol): Sends from port 143 to 993. Is standard email protocol for storing email messages on a mail server over SSL/TLS.
- Use cases:
- Voice and video: SRTP.
- Time synchronization: NTPsec.
- NTPsec (Secure network time protocol): Used to securely sync all the devices’ clocks on the network.
- Email and web: S/MIME and HTTPS.
- File transfer: FTPS or SFTP.
- Directory services: LDAPS or SASL.
- SASL (Simple Authentication and Security Layer): Provides a source of additional authentication using many different methods, such as Kerberos or client certificates.
- Remote access: SSH.
- Domain name resolution: DNSSec.
- Routing and switching: SNMPv3, SSH, or HTTPS.
- SNMPv3: Provides continentality, integrity, and authentication.
- HTTPS: Allows for browser-based management.
- Network address allocation: DHCP, there is no secure version it.
- DHCP starvation attack: Using spoofed MAC addresses to exhaust the amount of DHCP’s pool. Can configure a switch to limit the number of MAC addresses on an interface.
- Subscription services: Anti-viruses and anti-malware are subscription based. Must check regularly for updates. Set up integrity checks to verify the updates are coming from the correct source.












